A Timely Intervention: How Cowabunga Protected a local Resident from a Dangerous Scam
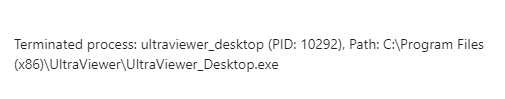
In the early hours of one recent morning, Cowabunga’s vigilant security system detected unusual activity on a client’s computer. At 4:55am, a remote access application was launched. While such applications can have genuine purposes, the timing was odd. Our security system quickly terminated the suspicious activity and we noted it, planning to notify the client at a more reasonable hour.
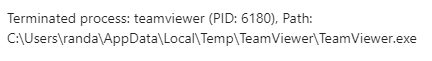
But by 5:16am, a second, different remote access application was flagged. Two such applications in such a short time span raised red flags. We knew immediate intervention was required.

Despite our best efforts, initial phone calls and on-screen alerts to the client went unanswered. Undeterred, we took further steps to ensure the client’s safety by shutting down active browser connections and other suspicious applications.
Finally, the client responded. They revealed they were on the phone with what they believed was “HP support”. They’d been instructed to ignore our calls and on-screen messages.
It became clear: our client was on the brink of becoming a victim of a technical support scam. A fraudulent search result had led them to a fake support line.
Thanks to Cowabunga’s unwavering commitment to security, the scam was thwarted. No credit card, bank, or retirement funds were compromised.
At Cowabunga, we pride ourselves on being more than just a managed services provider. We’re your frontline defense against the increasingly sophisticated world of cyber threats. Our message to all our valued clients and prospective partners: Let us be your first and only call for technical support. With Cowabunga in your corner, rest easy knowing you’re protected from the myriad of threats lurking online.
Choose Cowabunga for steadfast protection, always. Secure your computers, servers, and networks with the best in Honolulu.